Shift-Left Sensitive Data Protection
Prevent PII Leaks from the Source
Weeks lost chasing sensitive data across application logs?
Not anymore. HoundDog.ai flips the model by analyzing code early to catch unintentional developer mistakes that lead to the overlogging and oversharing of sensitive data, before it ever reaches production.
✅ Eliminate the chaos of reactive cleanups
🔐 Enforce privacy-by-design from day one
🛡️ Operationalize Zero Trust through proactive data minimization
📜 Stay compliant with GDPR, CCPA, HIPAA, PCI, FedRAMP, and other regulations
Continuous and Proactive Detection at the Speed of Development
For organizations holding critical data, the question is not if a breach will occur, but when. In 2023, customer and employee PII was the most commonly compromised record type, accounting for 92% of all breached data.
When sensitive information leaks through logs, files, or third-party systems, remediation becomes extremely costly. For example, if PII leaks into logs, relying on DLP is reactive, unreliable, and painfully slow – weeks are often wasted scrubbing logs, assessing exposure across every tool that ingested them, and patching code after the fact.
HoundDog.ai flips the model by analyzing code early – across the IDE, source control, and CI stages – to catch unintentional developer (or AI-generated) mistakes that lead to the overlogging and oversharing of sensitive data before it ever reaches production. We eliminate the chaos of reactive cleanups, enforce privacy-by-design from day one, and operationalize Zero Trust through proactive data minimization. Security teams stay ahead of growing privacy risks, maintain compliance with major regulations like GDPR, CCPA, HIPAA, PCI, and FedRAMP, and drastically reduce the blast radius of inevitable breaches.
92%
of all data compromised in 2023 involved customer and employee PII (Personally Identifiable Information) record types1
DevSecOps
ranked as the top data breach cost mitigator, with organizations that had high DevSecOps adoption saving USD 1.68 million compared to those with low or no adoption2
$4.45 M
average cost of a data breach in 20233
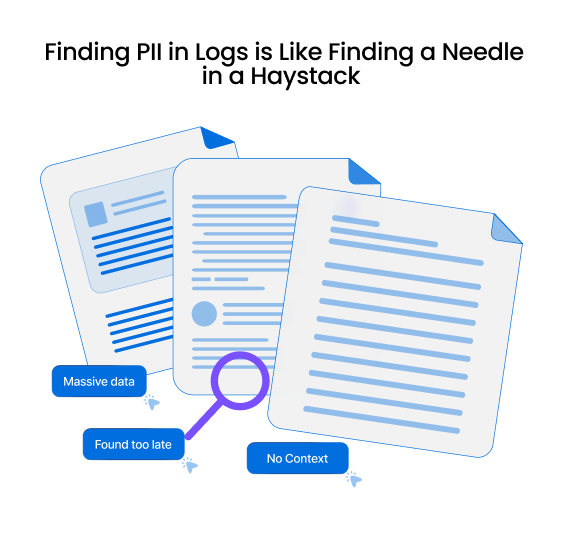
The Problem
PII Leaks Are Sneaky, Costly, and Often Caught Too Late
PII Overlogging & Oversharing. Developers unintentionally overlog and overshare PII across risky mediums such as logs, files, and third-party integrations. As teams grow, this risk escalates.
DLP’s Reactive & Unreliable Detection. Relying solely on DLP for PII detection in logs is reactive and unreliable due to sampling limitations. Issues are often identified too late—after logs have been ingested by multiple tools—without context on the root cause.
Data Sensitivity. AppSec teams struggle to prioritize risks effectively, relying on CVSS scores while neglecting data sensitivity. This leads to improper prioritization of vulnerabilities in code.
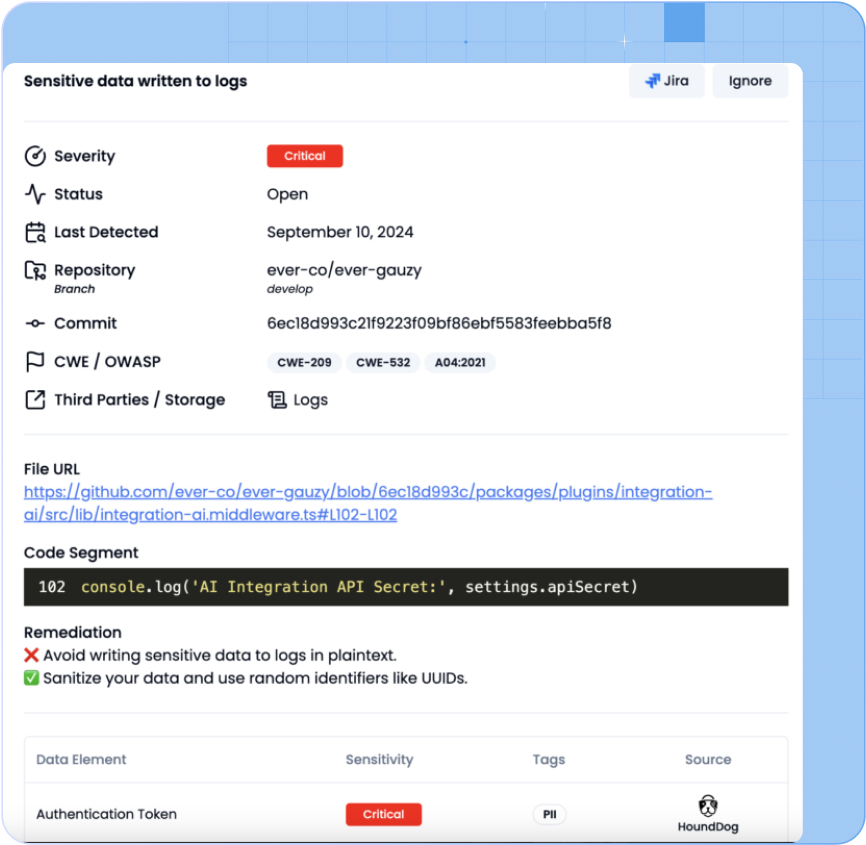
The Solution
Start PII Leak Detection And Data Flow Mapping Where It Matters Most: In the Code
HoundDog.ai for Proactive Sensitive Data Protection
-
Eliminate the chaos of reactive cleanups by enforcing privacy-by-design from day one, enabling proactive data minimization, and moving one step closer to an “Assume Breach” posture.
-
Expand AppSec coverage to detect unintentional developer mistakes that lead to overlogging and oversharing of sensitive data—issues that are difficult to identify and remediate in production—reducing the burden on your data security peers.
-
Enhance risk scoring by factoring in the sensitivity of data processed within application codebases - not all SQL injection vulnerabilities should be treated equally.
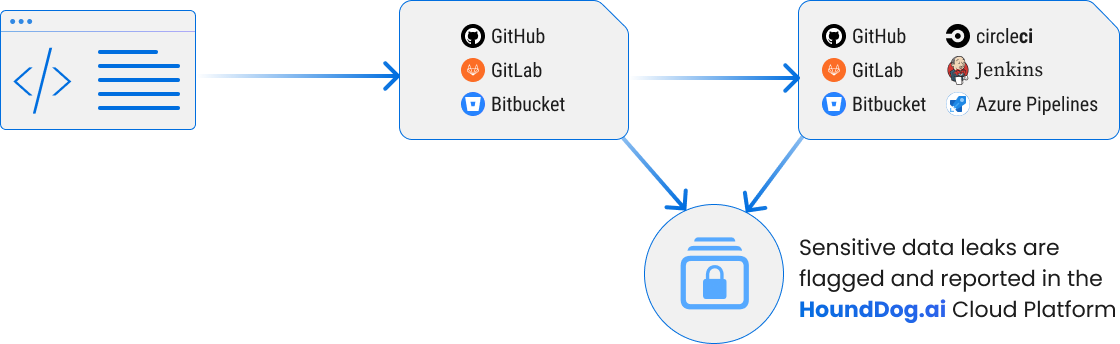
Enabling PII Leak Detection & Data Mapping Across All Stages of Development
IDE PLUGINS. (VS Code IntelliJ and Eclipse)
- Highlights PII leaks as code is being written
Managed Scans
- Offload scanning to HoundDog.ai with direct source control integrations
CI/CD Integrations
- Integrate the scanner into CI pipelines for pre-merge checks.

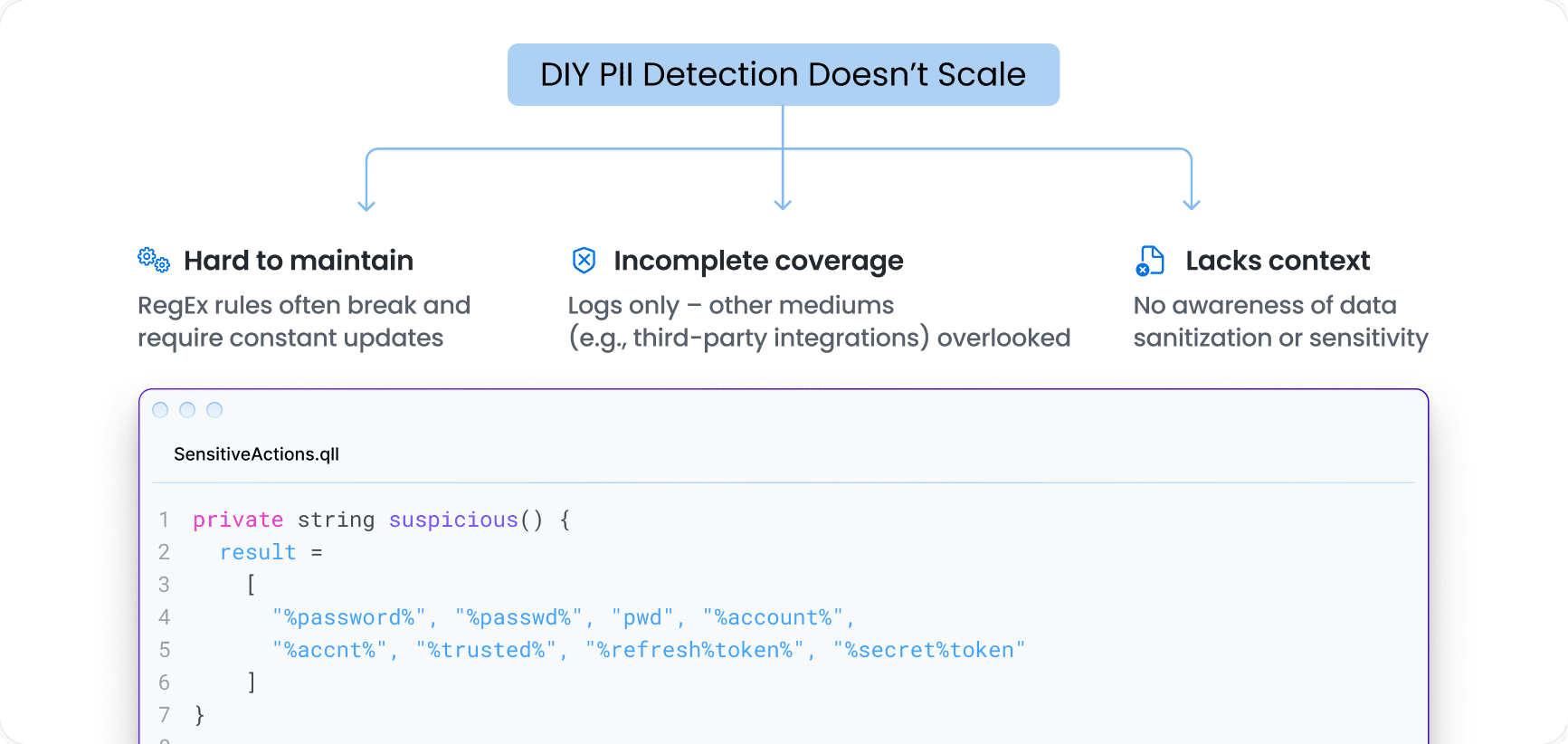
DIY PII Detection Doesn’t Scale
Hardcoded RegEx rules break easily and are a nightmare to maintain. Most DIY efforts stall before they scale
HoundDog.ai: Purpose-Built for PII Detection & Data Mapping
Unparalleled Coverage and Accuracy
Built-in detection with extensive coverage across:
- Sensitive data elements (PII, PHI, PIFI, CHD)
- Risky data sinks (including hundreds of third-party integrations)
- Sanitization functions (flag only when data isn’t properly sanitized)
Endless Flexibility
- Finetune detection across data elements, sinks, and sanitization to fit your environment.
Ready to Scale
- Connect to GitHub, GitLab, or Bitbucket to scan code, block PRs, and leave actionable comments—automatically.
- Managed Scans: Offload scanning to HoundDog.ai for continuous, hands-off coverage
- CI Jobs: Push CI configs to selected repos using your self-hosted runners, with options for direct commits or approval-based PRs
AI-Ready
- AI-powered detection that plugs into any LLM running in your environment—boosting coverage across data elements, sinks, and sanitization, while minimizing manual tuning. (Coming in Q2 2025)
Realize Significant Cost Reduction and Increased Productivity
ROI for proactive sensitive data protection
Make Privacy-by-Design a Reality in Your SDLC
Shift Left on Privacy. Scan Code. Get Evidence-Based Data Maps. Prevent PII Leaks in Logs and Other Risky Mediums Early—Before Weeks of Remediation in Production.