Introduction
Is your development team logging more data than necessary? This article looks at why developers often log excessive data to ensure application performance, even though this can clash with security practices. We’ll explore the reasons behind detailed logging, its security risks, and how to strike a balance between functionality and safety. By the end, you’ll learn how to optimize logging for better software performance and security.
Understanding the Developer vs. Security Professional Psyche
Developers want their apps to run smoothly and meet user needs, so they put a lot of effort into ensuring everything works perfectly. They use logs—a detailed diary of what the app does—to determine how everything works and fix any issues. This is important because it helps them see what’s happening under the hood and ensure everything ticks nicely.
On the other hand, security professionals are all about keeping the app safe from threats. They go through everything with a fine-tooth comb, especially the logs, to ensure nothing sensitive gets out.
They’re focused on keeping bad stuff from happening, so they’re always looking to clamp down on anything in the logs that might give away too much information.
There’s a natural tug-of-war between developers and security pros. Developers tend to log lots of details to keep the app humming and troubleshooting faster. But, this can sometimes spill secrets if not done carefully.
Security folks want to keep things tight and secure, which might mean reducing the detail in logs to protect sensitive data. Striking a tricky balance between ensuring the app works well and letting security slip is challenging.
Overlogging shows just how different the priorities are between the two groups. Developers log extensively to solve problems and get deep insights into the app, sometimes including sensitive info. Security teams see this as a risk—if those logs fall into the wrong hands, it could be a disaster.
They prefer keeping logs brief and secure to avoid leaks. Balancing deep insights with strong security is an ongoing challenge that is key to developing safe, effective software.
The Reasons Behind Developers’ Overlogging
Developers often use overlogging to find the root cause of issues faster. When something goes wrong, detailed logs can help pinpoint exactly where the problem started.
It’s like having a detailed map when you’re lost; the more information you have, the quicker you can find your way back. This approach can be especially helpful in complex systems where errors might be subtle or masked by other processes.
Sometimes, developers log extensively out of habit or precaution. Even if they’re unsure that all the information will be useful, the fear of missing crucial details during a future problem-solving session can lead to logging everything “just in case.”
This mindset can result in a massive amount of data, much of which may never be used, but the peace of mind it provides developers is often worth the extra effort.
Security Risks Associated with Overlogging
Increased attack surface area due to excessive logs
When developers log too much information, they can inadvertently increase an application’s attack surface. Each piece of logged data, especially if not adequately protected, becomes a potential entry point for attackers.
Logs that aren’t securely managed and restricted can be accessed or intercepted, giving malicious individuals more opportunities to exploit vulnerabilities. This is particularly risky when logs are stored without sufficient security measures or transmitted over unsecured channels.
Vulnerabilities identified by OWASP ASVS, CWE-532, and CWE-210
The OWASP Application Security Verification Standard (ASVS) and Common Weakness Enumeration (CWE) provide guidelines and list common vulnerabilities that can arise from improper handling of logs. CWE-532 and CWE-210, for instance, focus on logging Personal Identifiable Information (PII).
Logging sensitive data without proper controls breaches privacy norms and violates compliance regulations. This is especially critical in applications that may not be mission-critical but still handle sensitive data. These apps might have different levels of security scrutiny, making them vulnerable targets for data breaches.
Implications for non-mission-critical apps
Non-mission-critical applications often have less stringent security measures, making them prime targets for data breaches if they log sensitive information.
Developers might need to pay more attention to the security needs of such apps, assuming they won’t be attractive targets for attacks. However, any application that logs PII must enforce strict controls to protect that data from unauthorized access.
The real-world impact of overlogging can be severe. Numerous incidents have occurred where excessive PII logging led to significant security breaches, resulting in massive compliance violations and financial penalties.
These breaches lead to direct financial loss and damage customers’ trust in a company’s ability to protect their personal information.
Moreover, once this trust is broken, rebuilding can be tough, affecting the company’s reputation and customer relationships in the long term. This shows the critical importance of having a disciplined approach to logging, ensuring that only necessary data is logged and is done so securely.
The Challenges of Remediating PII Data in Logs
Addressing the issue of PII data in logs is no small task. It often involves multiple steps, including updating the code to prevent sensitive data from being logged in the first place.
Developers need to sift through existing logs to identify and remove PII, which requires meticulous review and an understanding of what constitutes sensitive information under various compliance frameworks.
Additionally, risk assessments must be conducted to understand the potential impacts of exposed data and to ensure that similar vulnerabilities are mitigated in the future. Each step requires significant time and expertise, making remediation a complex challenge.
Lastly, when PII is found in a log, it doesn’t just stay there. It often propagates to all systems ingesting those logs, including monitoring, observability, SIEM, backups, etc. Suddenly, the blast radius becomes much larger, and security teams are left playing a game of whack-a-mole, trying to clean up the data across these platforms while navigating the various data handling protocols of third-party systems.
Legal and Reputational Risks: Notifications and Compliance
When PII is mishandled, the fallout can extend beyond the technical realm into legal and reputational areas. Companies may face legal repercussions if they fail to comply with data protection laws, such as GDPR or HIPAA. This could lead to hefty fines and mandatory corrective actions.
Moreover, if a breach occurs and customers’ data is compromised, notifying affected individuals is not just a legal requirement—it’s a crucial step in managing the company’s reputation. Mishandling such notifications can further erode trust and deter customers from continuing to engage with the business.
Remediating PII data in logs is also a resource-heavy endeavor. It demands considerable technical resources, including dedicated staff to manage the remediation process and advanced tools to erase or modify sensitive data securely.
Financial resources are equally important, as investing in better logging practices and security measures can be costly. Moreover, the time spent identifying, rectifying, and preventing PII exposure in logs diverts attention from other development and security priorities, adding to the overall resource strain.
The Need for Proactive Sensitive Data Protection
Putting security measures right into the code from the beginning is super important. When developers think about security as they write the code, it makes a big difference in keeping data safe.
This means encrypting data when it’s sent or stored, following best practices to avoid common coding mistakes, and setting up rules about who can see what data. By baking these practices into the code early, the app helps keep sensitive information, like personal details, secure throughout its life.
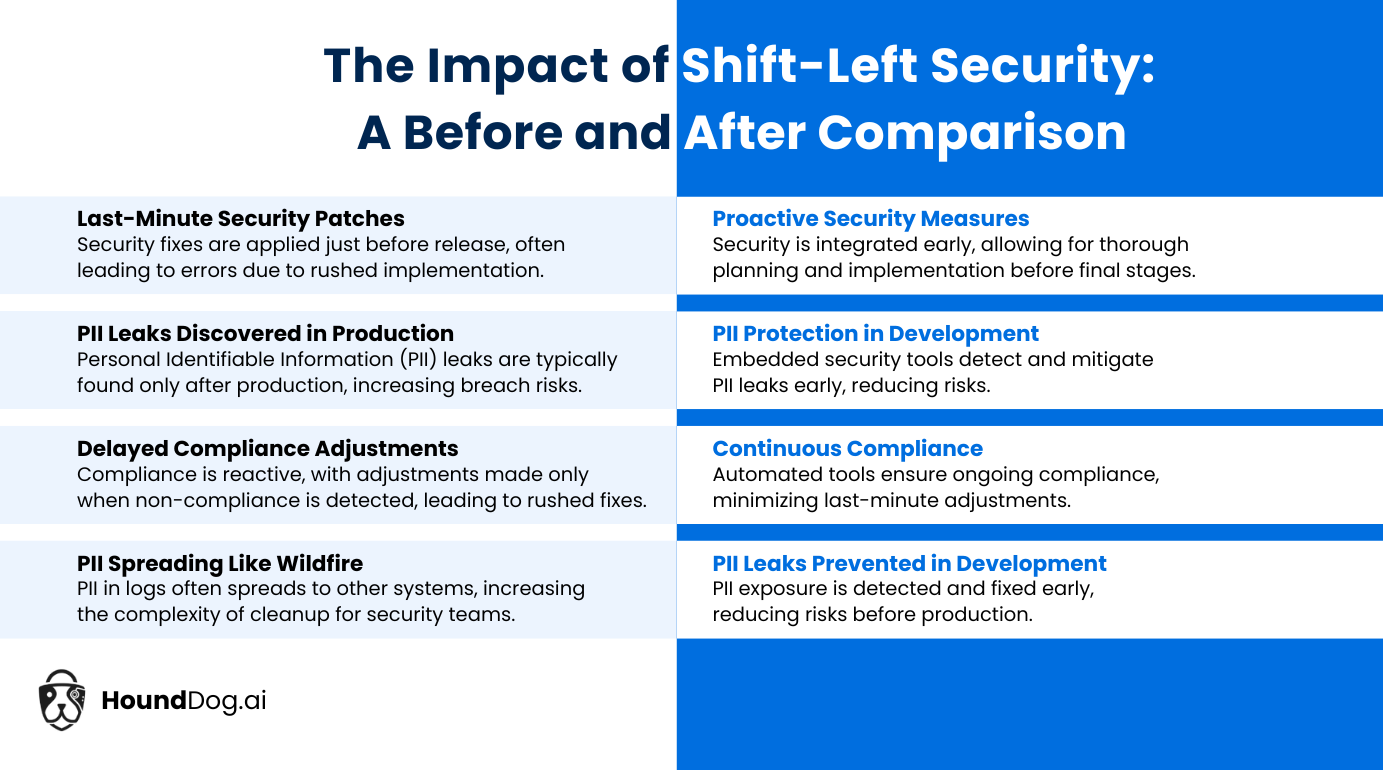
Shift-Left to Prevent PII Leaks and Overlogging
Starting with security in mind from the early stages of development—or shifting it left—has some great perks. This approach catches problems early when they’re usually cheaper and easier to fix. It also means less chance of private information getting out by mistake.
This includes conducting regular security checks, reviewing code carefully, and ensuring developers know how to spot and handle security issues. The earlier these practices are adopted, the less likely unnecessary or risky data will be logged, making the whole app safer.
Integrating Security Tools to Prevent Excessive Data Logging
Bringing security tools into the development process is key to keeping private data safe and avoiding unnecessary logging. Tools like AI-powered code scanners help catch vulnerabilities automatically as developers write code. They work in the background, spotting risks and offering fixes before the app goes live.
Also, setting up automatic systems to ensure data handling meets privacy laws helps keep everything on track without slowing development. This combination of smart tools and automation makes building secure apps more straightforward and less error-prone.
Conclusion
We’ve covered why developers log a lot of data, the security risks this brings, and the legal challenges, especially with handling Personally Identifiable Information (PII). Logs are important for troubleshooting and improving functionality, but they need to be secured to protect sensitive data. Early security measures and advanced tools can help manage these risks. To see how we can help, book a demo with HoundDog and learn how our security solutions can improve your software development.