The Inspiration Behind This Company
It’s a big day for HoundDog.ai. We’re coming out of stealth, announcing our Series Seed round of funding and the launch of our platform. Read all about it, here.
Before my co-founders and I started HoundDog.ai, I served as the VP of Product at a data security company, specializing in discovering, classifying, and applying access controls to sensitive data in production. During this time, I encountered numerous concerns from security and privacy teams, who were frustrated with the reactive data security and privacy measures that struggled to keep pace with rapid changes in their applications’ codebases.
This frustration sparked the idea for HoundDog.ai. Common questions from these teams included:
- “How can I prevent PII data from leaking in the first place, rather than catching it once it’s already in production logs, files, or third-party systems?”
- “How can we establish a reliable method for documenting processing activities that keeps up with changes in our codebase without relying on inconsistent tribal knowledge?”
- “How can my privacy engineers stay ahead of product changes that introduce new data collections requiring lawful processing?”
Our founding team had several well-informed ideas about how to address these issues, and that led to the creation of HoundDog.ai.
Proactive vs. Reactive Data Security
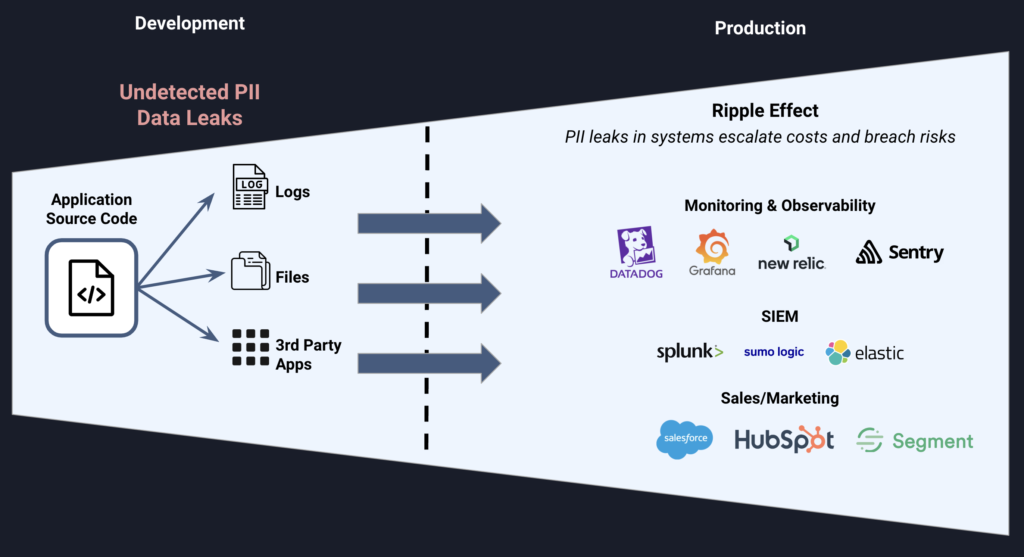
For too long, organizations have succumbed to a reactive approach to data leak detection and remediation. In 2023, 92% of compromised data involved PII records. Remediation of sensitive data leaks can be very expensive, requiring code updates, access log reviews, incident reporting, and, in some cases, customer notifications. Although many organizations are aware of the structured data they have in their production environments, undetected PII leaks (through logs, files or third-party systems) can trigger cascading issues across various systems, increasing both the risk and cost of mitigation. Currently, most companies depend on data security and DLP platforms that only respond once data has entered production—a practice that increases risk, complexity, and cost.
Challenges in Privacy Compliance
Creating GDPR-compliant processing activity records is crucial but challenging, often hindered by outdated data maps that fail to keep pace with product development. Privacy teams frequently find themselves caught off-guard by new product features that process personal data in non-compliant ways.
The Limitations of SAST Scanners
One might expect that SAST scanners could detect these PII leaks before code is merged and pushed to production. However, today’s SAST scanners are unable to detect sensitive data flows for many reasons. For instance, while SAST scanners that rely on pattern matching rules work well when such patterns are predictable (e.g., an insecure gRPC connection using ‘grpc.WithInsecure()’), they struggle with identifying code logic handling sensitive data like social security numbers, where developers may use varied names for functions or methods handling such data. Moreover, when it comes to mapping data flows throughout an entire codebase, SAST scanners struggle to connect the dots across multiple files and data sinks.
Introducing HoundDog.ai: An AI-Powered Code Scanner to Stop PII Leaks at the Source and Automate Data Mapping for GDPR Compliance
HoundDog.ai addresses the aforementioned challenges by leveraging AI and an extensive library of finely tuned definitions for sensitive data, encompassing most PII, PIFI, and PHI data. Unlike current SAST scanners, the AI workflow was built from the beginning and not bolted on after the fact. The scanner uses advanced code analysis to enhance true positive detection and map data flows, including interprocedural analysis and taint analysis to identify manipulated variables across the codebase.
This scanner continuously detects vulnerabilities that SAST scanners miss—namely, those that expose sensitive data in plaintext across various mediums, such as logs, files, tokens, cookies, or through third-party systems. Additionally, HoundDog.ai tracks and visualizes the flow of sensitive data and facilitates the generation of Records of Processing Activities (RoPA) with just a few clicks. It also alerts users when new data elements are introduced, based on their sensitivity levels, to prevent out-of-scope product changes from going live and to avoid privacy incidents. See how it works using our interactive demos.
Fast, Extensible, and Enterprise-Ready
Our scanner quickly analyzes over 3 million lines of code in under three minutes. It supports a wide range of programming languages, integrates seamlessly with most CI pipelines, and delivers findings directly into GitHub and GitLab security dashboards, with alerts also available through Slack and Jira. The platform is SOC-2 compliant, supports single sign-on (SSO), and maintains standardized audit logs.
Try Our Free Scanner
HoundDog.ai offers a free scanner that provides a full data map of sensitive data flows within a codebase. These data flow reports are a critical requirement for documenting processing activities for GDPR compliance and are needed for other security audits as well. Access the scanner here. We’re excited about today’s news, and we’re already engaged with early access customers who are using HoundDog.ai to solve problems that were intractable before.